Eurostat European Commission: Difference between revisions
Jump to navigation
Jump to search
mNo edit summary |
Norah.Shamin (talk | contribs) |
||
| (9 intermediate revisions by 2 users not shown) | |||
| Line 1: | Line 1: | ||
__FORCETOC__ | __FORCETOC__ | ||
= Summary = | |||
<div style="display:flex; flex-flow: column wrap; text-align: left;"> | <div style="display:flex; flex-flow: column wrap; text-align: left;"> | ||
[https://ec.europa.eu/eurostat/web/main/home Eurostat] is a Directorate-General of the European Commission which is the statistical office of the European Union (EU). Eurostat collects and publishes aggregate data on various variables in EU countries. Users can rely on the Eurostat database to find a number of data series and variables such as: SeriesICTCybEnterprises%ISDNConnection, SeriesICTCybEnterprises%MobileBroadbandConnection, SeriesICTCybEnterprises%SecFacOffStorage, and SeriesICTCybEnterprisesC%SecPolicyDataLoss. | |||
== | = Tables In IFs = | ||
{| class="wikitable" | |||
!Variables | |||
!Definition | |||
!Source Ext Def | |||
!LastIFsUpdate | |||
!Name In Source | |||
!UsedInPreprocessor | |||
|- | |||
|PovRateNPLBothSexesEuroStat | |||
|At risk of poverty rate (cut-off point: 60% of median equivalised income after social transfers), all ages, both sexes, from EuroStat | |||
| | |||
|7/5/2021 | |||
|Income and living conditions indicator: At risk of poverty rate | |||
|0 | |||
|- | |||
|PovRateNPLFemaleEuroStat | |||
|At risk of poverty rate (cut-off point: 60% of median equivalised income after social transfers), all ages, female, from EuroStat | |||
| | |||
|7/5/2021 | |||
|Income and living conditions indicator: At risk of poverty rate | |||
|0 | |||
|- | |||
|PovRateNPLMaleEuroStat | |||
|At risk of poverty rate (cut-off point: 60% of median equivalised income after social transfers), all ages, male, from EuroStat | |||
| | |||
|7/5/2021 | |||
|Income and living conditions indicator: At risk of poverty rate | |||
|0 | |||
|- | |||
|ICTVA%GDP | |||
|ICT value added as % of GDP | |||
|OECD Key ICT Indicators, 10b. R&D expenditure in selected ICT industries, 2005contact Geomina, Geomina.TURLEA@ec.europa.eu and Jonathan Moyer | |||
|9/14/2010 | |||
| | |||
|0 | |||
|- | |||
|R&Dbus%GDP | |||
|R&D, business expenditure as a % of GDP | |||
|contact Geomina, Geomina.TURLEA@ec.europa.eu and Jonathan Moyer | |||
|9/14/2010 | |||
| | |||
|0 | |||
|- | |||
|R&DICTBus%GDP | |||
|R&D in ICT, business expenditure, as a percentage of GDP | |||
|contact Geomina, Geomina.TURLEA@ec.europa.eu and Jonathan Moyer | |||
|9/14/2010 | |||
| | |||
|0 | |||
|- | |||
|R&DICTBus%ICTVA | |||
|R&D in ICT, business expenditure, as a % of ICT value added | |||
|contact Geomina, Geomina.TURLEA@ec.europa.eu and Jonathan Moyer | |||
|9/14/2010 | |||
| | |||
|0 | |||
|- | |||
|R&DICTBus%Total | |||
|R&D in ICT, business expenditure, as a % of total business expenditure on R & D | |||
|contact Geomina, Geomina.TURLEA@ec.europa.eu and Jonathan Moyer | |||
|9/14/2010 | |||
| | |||
|0 | |||
|- | |||
|R&DICTGovt%GDP | |||
|R&D in ICT, public expenditure, as a % of GDP | |||
|OECD Key ICT Indicators, 10b. R&D expenditure in selected ICT industries, 2005contact Geomina, Geomina.TURLEA@ec.europa.eu and Jonathan Moyer | |||
|9/14/2010 | |||
| | |||
|0 | |||
|- | |||
|ICTBroadbandHouseholdEStat | |||
|% of households using a broadband connection | |||
|% of hhs using a broadband connection | |||
|2/15/2009 | |||
|% of hhs using a broadband connection | |||
|0 | |||
|- | |||
|ICTBroadbandHouseholdIIACEStat | |||
|% of households with internet access using a broadband connection | |||
|% of households with internet access using a broadband connection | |||
|2/15/2009 | |||
|% of households with internet access using a broadband connection | |||
|0 | |||
|- | |||
|ICTBuyOnlineIndividual | |||
|% of individuals with internet access that have ordered via internet over last calendar year | |||
|% of individuals with internet access that have ordered via internet over last calendar year | |||
|3/1/2009 | |||
|% of firms with internet access that have ordered via internet over last calendar year | |||
|0 | |||
|- | |||
|ICTCybEnterprises%ISDNConnection | |||
|The percentage of enterprises connecting to the Internet via ISDN | |||
|The percentage of enterprises connecting to the Internet via ISDN. | |||
|5/5/2015 | |||
| | |||
|0 | |||
|- | |||
|ICTCybEnterprises%MobileBroadbandConnection | |||
|The percentage of enterprises connecting to the Internet via a mobile broadband connection (3G modem or 3G handset). | |||
|The percentage of enterprises connecting to the Internet via a mobile broadband connection (3G modem or 3G handset). | |||
|5/5/2015 | |||
| | |||
|0 | |||
|- | |||
|ICTCybEnterprises%MobileConnection | |||
|The percentage of enterprises connecting to the Internet via a mobile connection (e.g. mobile phone, GPRS, UMTS, etc.). | |||
|The percentage of enterprises connecting to the Internet via a mobile connection (e.g. mobile phone, GPRS, UMTS, etc.). | |||
|5/5/2015 | |||
| | |||
|0 | |||
|- | |||
|ICTCybEnterprises%MobileConnection2014 | |||
|The percentage of enterprises connecting to the Internet via mobile connection (broadband or other mobile connection) | |||
|The percentage of enterprises connecting to the Internet via mobile connection (broadband or other mobile connection) | |||
|5/5/2015 | |||
| | |||
|0 | |||
|- | |||
|ICTCybEnterprises%ModemConnection | |||
|The percentage of enterprises connecting to the Internet via modem (dial-up access over normal telephone line). | |||
|The percentage of enterprises connecting to the Internet via modem (dial-up access over normal telephone line). | |||
|5/5/2015 | |||
| | |||
|0 | |||
|- | |||
|ICTCybEnterprises%SecFacID | |||
|Percent of enterprises using strong password authentication (min 8 characters, max 6 months, encrypted transmission and storage) and user identification and authentication via hardware tokens, e.g. smart cards | |||
|Percent of enterprises using strong password authentication (min 8 characters, max 6 months, encrypted transmission and storage) and user identification and authentication via hardware tokens, e.g. smart cards | |||
|5/6/2015 | |||
| | |||
|0 | |||
|- | |||
|ICTCybEnterprises%SecFacIDHW | |||
|Percent of enterprises using user identification and authentication via hardware tokens, e.g. smart cards | |||
|Percent of enterprises using user identification and authentication via hardware tokens, e.g. smart cards | |||
|5/6/2015 | |||
| | |||
|0 | |||
|- | |||
|ICTCybEnterprises%SecFacLog | |||
|Percent of enterprises logging activities for analyses of security incidents | |||
|Percent of enterprises logging activities for analyses of security incidents | |||
|5/6/2015 | |||
| | |||
|0 | |||
|- | |||
|ICTCybEnterprises%SecFacOffStorage | |||
|Percent of enterprises storing data backups offsite | |||
|Percent of enterprises storing data backups offsite | |||
|5/6/2015 | |||
| | |||
|0 | |||
|- | |||
|ICTCybEnterprises%SecFacPW | |||
|Percent of enterprises using strong password authentication (min 8 characters, max 6 months, encrypted transmission and storage) | |||
|Percent of enterprises using strong password authentication (min 8 characters, max 6 months, encrypted transmission and storage) | |||
|5/6/2015 | |||
| | |||
|0 | |||
|- | |||
|ICTCybEnterprises%SecIncidentAllEx | |||
|Percent of enterprises that exxperienced any ICT related security incidents excluding disclosure of confidential data in electronic form by employees. | |||
|Percent of enterprises that exxperienced any ICT related security incidents excluding disclosure of confidential data in electronic form by employees. | |||
|5/6/2015 | |||
| | |||
|0 | |||
|- | |||
|ICTCybEnterprises%SecIncidentConfData | |||
|Percent of enterprises that experienced ICT related security incidents that resulted in disclosure of confidential data due to intrusion, pharming, phishing attacks. | |||
|Percent of enterprises that experienced ICT related security incidents that resulted in disclosure of confidential data due to intrusion, pharming, phishing attacks. | |||
|5/6/2015 | |||
| | |||
|0 | |||
|- | |||
|ICTCybEnterprises%SecIncidentDataLoss | |||
|Percent of enterprises that experienced ICT related security incidents that resulted in destruction or corruption of data due to infection or malicious software or unauthorised access. | |||
|Percent of enterprises that experienced ICT related security incidents that resulted in destruction or corruption of data due to infection or malicious software or unauthorised access. | |||
|5/6/2015 | |||
| | |||
|0 | |||
|- | |||
|ICTCybEnterprises%SecIncidentEmploy | |||
|Percent of enterprises that experienced ICT related security incidents resulting in disclosure of confidential data in electronic form by employees whether on intention or unintentionally. | |||
|Percent of enterprises that experienced ICT related security incidents resulting in disclosure of confidential data in electronic form by employees whether on intention or unintentionally. | |||
|5/6/2015 | |||
| | |||
|0 | |||
|- | |||
|ICTCybEnterprises%SecIncidentNone | |||
|Percent of enterprises that did not experience any ICT related security incidents excluding disclosure of confidential data in electronic form by employees. | |||
|Percent of enterprises that did not experience any ICT related security incidents excluding disclosure of confidential data in electronic form by employees. | |||
|5/6/2015 | |||
| | |||
|0 | |||
|- | |||
|ICTCybEnterprises%SecIncidentOutThreat | |||
|Percent of enterprises that experienced ICT related security incidents that resulted in unavailability of ICT services due to attacks from outside, e.g. Denial of Service attack. | |||
|Percent of enterprises that experienced ICT related security incidents that resulted in unavailability of ICT services due to attacks from outside, e.g. Denial of Service attack. | |||
|5/6/2015 | |||
| | |||
|0 | |||
|- | |||
|ICTCybEnterprises%SecIncidentSystemFailure | |||
|Percent of enterprises that experienced ICT related security incidents that resulted in unavailability of ICT services, destruction or corruption of data due to hardware or software failures. | |||
|Percent of enterprises that experienced ICT related security incidents that resulted in unavailability of ICT services, destruction or corruption of data due to hardware or software failures. | |||
|5/6/2015 | |||
| | |||
|0 | |||
|- | |||
|ICTCybEnterprises%SecPolicy | |||
|Percent of enterprises that have a formally defined ICT security policy with a plan of regular review. | |||
|Percent of enterprises that have a formally defined ICT security policy with a plan of regular review. | |||
|5/6/2015 | |||
| | |||
|0 | |||
|- | |||
|ICTCybEnterprises%SecPolicyAll | |||
|Percent of enterprises whose ICT security policy addressed the risks of destruction or corruption of data, disclosure of confidential data and unavailability of ICT services due to an attack or an accident. | |||
|Percent of enterprises whose ICT security policy addressed the risks of destruction or corruption of data, disclosure of confidential data and unavailability of ICT services due to an attack or an accident. | |||
|5/6/2015 | |||
| | |||
|0 | |||
|- | |||
|ICTCybEnterprises%SecPolicyConfData | |||
|Percent of enterprises whose ICT security policy addressed the risks of disclosure of confidential data due to intrusion, pharming, phishing attacks or by accident. | |||
|Percent of enterprises whose ICT security policy addressed the risks of disclosure of confidential data due to intrusion, pharming, phishing attacks or by accident. | |||
|5/6/2015 | |||
| | |||
|0 | |||
|- | |||
|ICTCybEnterprises%SecPolicyDataLoss | |||
|Percent of enterprises whose ICT security policy addressed the risks of destruction or corruption of data due to an attack or by unexpected incident. | |||
|Percent of enterprises whose ICT security policy addressed the risks of destruction or corruption of data due to an attack or by unexpected incident. | |||
|5/6/2015 | |||
| | |||
|0 | |||
|- | |||
|ICTCybEnterprises%SecPolicyOutThreat | |||
|Percent of enterprises whose ICT security policy addressed the risks of unavailability of ICT services due to an attack from outside (e.g. Denial of Service attack). | |||
|Percent of enterprises whose ICT security policy addressed the risks of unavailability of ICT services due to an attack from outside (e.g. Denial of Service attack). | |||
|5/6/2015 | |||
| | |||
|0 | |||
|- | |||
|ICTCybEnterprises%Website | |||
|The percentage of enterprises that have a website or homepage. | |||
|The percentage of enterprises that have a website or homepage. | |||
|5/5/2015 | |||
| | |||
|0 | |||
|- | |||
|ICTCybEnterprises%WirelessConnection | |||
|The percentage of all enterprises connecting to the Internet via wireless connection (satellite, mobile phone). | |||
|The percentage of all enterprises connecting to the Internet via wireless connection (satellite, mobile phone). | |||
|5/5/2015 | |||
| | |||
|0 | |||
|- | |||
|ICTCybEnterprisesC%SecFacID | |||
|Percent of enterprises with computers using strong password authentication (min 8 characters, max 6 months, encrypted transmission and storage) and user identification and authentication via hardware tokens, e.g. smart cards | |||
|Percent of enterprises using strong password authentication (min 8 characters, max 6 months, encrypted transmission and storage) and user identification and authentication via hardware tokens, e.g. smart cards | |||
|5/6/2015 | |||
| | |||
|0 | |||
|- | |||
|ICTCybEnterprisesC%SecFacIDHW | |||
|Percent of enterprises with computers using user identification and authentication via hardware tokens, e.g. smart cards | |||
|Percent of enterprises using user identification and authentication via hardware tokens, e.g. smart cards | |||
|5/6/2015 | |||
| | |||
|0 | |||
|- | |||
|ICTCybEnterprisesC%SecFacLog | |||
|Percent of enterprises with computers logging activities for analyses of security incidents | |||
|Percent of enterprises logging activities for analyses of security incidents | |||
|5/6/2015 | |||
| | |||
|0 | |||
|- | |||
|ICTCybEnterprisesC%SecFacOffStorage | |||
|Percent of enterprises with computers storing data backups offsite | |||
|Percent of enterprises storing data backups offsite | |||
|5/6/2015 | |||
| | |||
|0 | |||
|- | |||
|ICTCybEnterprisesC%SecFacPW | |||
|Percent of enterprises with computers using strong password authentication (min 8 characters, max 6 months, encrypted transmission and storage) | |||
|Percent of enterprises using strong password authentication (min 8 characters, max 6 months, encrypted transmission and storage) | |||
|5/6/2015 | |||
| | |||
|0 | |||
|- | |||
|ICTCybEnterprisesC%SecIncidentAllEx | |||
|Percent of enterprises with computers that experienced any ICT related security incidents excluding disclosure of confidential data in electronic form by employees. | |||
|Percent of enterprises with computers that experienced any ICT related security incidents excluding disclosure of confidential data in electronic form by employees. | |||
|5/6/2015 | |||
| | |||
|0 | |||
|- | |||
|ICTCybEnterprisesC%SecIncidentConfData | |||
|Percent of enterprises with computers that experienced ICT related security incidents that resulted in disclosure of confidential data due to intrusion, pharming, phishing attacks. | |||
|Percent of enterprises with computers that experienced ICT related security incidents that resulted in disclosure of confidential data due to intrusion, pharming, phishing attacks. | |||
|5/6/2015 | |||
| | |||
|0 | |||
|- | |||
|ICTCybEnterprisesC%SecIncidentDataLoss | |||
|Percent of enterprises with computers that experienced ICT related security incidents that resulted in destruction or corruption of data due to infection or malicious software or unauthorised access. | |||
|Percent of enterprises with computers that experienced ICT related security incidents that resulted in destruction or corruption of data due to infection or malicious software or unauthorised access. | |||
|5/6/2015 | |||
| | |||
|0 | |||
|- | |||
|ICTCybEnterprisesC%SecIncidentEmploy | |||
|Percent of enterprises with computers that experienced ICT related security incidents resulting in disclosure of confidential data in electronic form by employees whether on intention or unintentionally. | |||
|Percent of enterprises with computers that experienced ICT related security incidents resulting in disclosure of confidential data in electronic form by employees whether on intention or unintentionally. | |||
|5/6/2015 | |||
| | |||
|0 | |||
|- | |||
|ICTCybEnterprisesC%SecIncidentNone | |||
|Percent of enterprises with computers that did not experienced any ICT related security incidents excluding disclosure of confidential data in electronic form by employees. | |||
|Percent of enterprises with computers that did not experienced any ICT related security incidents excluding disclosure of confidential data in electronic form by employees. | |||
|5/6/2015 | |||
| | |||
|0 | |||
|- | |||
|ICTCybEnterprisesC%SecIncidentOutThreat | |||
|Percent of enterprises with computers that experienced ICT related security incidents that resulted in unavailability of ICT services due to attacks from outside, e.g. Denial of Service attack. | |||
|Percent of enterprises with computers that experienced ICT related security incidents that resulted in unavailability of ICT services due to attacks from outside, e.g. Denial of Service attack. | |||
|5/6/2015 | |||
| | |||
|0 | |||
|- | |||
|ICTCybEnterprisesC%SecIncidentSystemFailure | |||
|Percent of enterprises with computers that experienced ICT related security incidents that resulted in unavailability of ICT services, destruction or corruption of data due to hardware or software failures. | |||
|Percent of enterprises with computers that experienced ICT related security incidents that resulted in unavailability of ICT services, destruction or corruption of data due to hardware or software failures. | |||
|5/6/2015 | |||
| | |||
|0 | |||
|- | |||
|ICTCybEnterprisesC%SecPolicy | |||
|Percent of enterprises which use computers that have a formally defined ICT security policy with a plan of regular review. | |||
|Percent of enterprises that have a formally defined ICT security policy with a plan of regular review. | |||
|5/6/2015 | |||
| | |||
|0 | |||
|- | |||
|ICTCybEnterprisesC%SecPolicyAll | |||
|Percent of enterprises which use computers whose ICT security policy addressed the risks of destruction or corruption of data, disclosure of confidential data and unavailability of ICT services due to an attack or an accident. | |||
|Percent of enterprises which use computers whose ICT security policy addressed the risks of destruction or corruption of data, disclosure of confidential data and unavailability of ICT services due to an attack or an accident. | |||
|5/6/2015 | |||
| | |||
|0 | |||
|- | |||
|ICTCybEnterprisesC%SecPolicyConfData | |||
|Percent of enterprises which use computers whose ICT security policy addressed the risks of disclosure of confidential data due to intrusion, pharming, phishing attacks or by accident. | |||
|Percent of enterprises which use computers whose ICT security policy addressed the risks of disclosure of confidential data due to intrusion, pharming, phishing attacks or by accident. | |||
|5/6/2015 | |||
| | |||
|0 | |||
|- | |||
|ICTCybEnterprisesC%SecPolicyDataLoss | |||
|Percent of enterprises which use computers whose ICT security policy addressed the risks of destruction or corruption of data due to an attack or by unexpected incident. | |||
|Percent of enterprises which use computers whose ICT security policy addressed the risks of destruction or corruption of data due to an attack or by unexpected incident. | |||
|5/6/2015 | |||
| | |||
|0 | |||
|- | |||
|ICTCybEnterprisesC%SecPolicyOutThreat | |||
|Percent of enterprises which use computers whose ICT security policy addressed the risks of unavailability of ICT services due to an attack from outside (e.g. Denial of Service attack). | |||
|Percent of enterprises which use computers whose ICT security policy addressed the risks of unavailability of ICT services due to an attack from outside (e.g. Denial of Service attack). | |||
|5/6/2015 | |||
| | |||
|0 | |||
|- | |||
|ICTCybEnterprisesIA%ISDNConnection | |||
|The percentage of enterprises with internet access connecting to the Internet via ISDN | |||
|The percentage of enterprises with internet access connecting to the Internet via ISDN | |||
|5/5/2015 | |||
| | |||
|0 | |||
|- | |||
|ICTCybEnterprisesIA%MobileBroadbandConnection | |||
|The percentage of enterprises with internet access connecting to the Internet via a mobile broadband connection (3G modem or 3G handset). | |||
|The percentage of enterprises with internet access connecting to the Internet via a mobile broadband connection (3G modem or 3G handset). | |||
|5/5/2015 | |||
| | |||
|0 | |||
|- | |||
|ICTCybEnterprisesIA%MobileConnection | |||
|The percentage of enterprises with internet access connecting to the Internet via a mobile connection (e.g. mobile phone, GPRS, UMTS, etc.). | |||
|The percentage of enterprises with internet access connecting to the Internet via a mobile connection (e.g. mobile phone, GPRS, UMTS, etc.). | |||
|5/5/2015 | |||
| | |||
|0 | |||
|- | |||
|ICTCybEnterprisesIA%MobileConnection2014 | |||
|The percentage of enterprises with internet access connecting to the Internet via mobile connection (broadband or other mobile connection) | |||
|The percentage of enterprises with internet access connecting to the Internet via mobile connection (broadband or other mobile connection) | |||
|5/5/2015 | |||
| | |||
|0 | |||
|- | |||
|ICTCybEnterprisesIA%ModemConnection | |||
|The percentage of enterprises with internet access connecting to the Internet via modem (dial-up access over normal telephone line). | |||
|The percentage of enterprises with internet access connecting to the Internet via modem (dial-up access over normal telephone line). | |||
|5/5/2015 | |||
| | |||
|0 | |||
|- | |||
|ICTCybEnterprisesIA%WirelessConnection | |||
|The percentage of enterprises with internet access connecting to the Internet via wireless connection (satellite, mobile phone). | |||
|The percentage of enterprises with internet access connecting to the Internet via wireless connection (satellite, mobile phone). | |||
|5/5/2015 | |||
| | |||
|0 | |||
|- | |||
|ICTCybEnterprisesICT%SecPolicyAll | |||
|Percent of enterprises which have an ICT security policy whose security policy addressed the risks of destruction or corruption of data, disclosure of confidential data and unavailability of ICT services due to an attack or an accident. | |||
|Percent of enterprises which have an ICT security policy whose security policy addressed the risks of destruction or corruption of data, disclosure of confidential data and unavailability of ICT services due to an attack or an accident. | |||
|5/6/2015 | |||
| | |||
|0 | |||
|- | |||
|ICTCybEnterprisesICT%SecPolicyConfData | |||
|Percent of enterprises which have an ICT security policy whose security policy addressed the risks of disclosure of confidential data due to intrusion, pharming, phishing attacks or by accident. | |||
|Percent of enterprises which have an ICT security policy whose security policy addressed the risks of disclosure of confidential data due to intrusion, pharming, phishing attacks or by accident. | |||
|5/6/2015 | |||
| | |||
|0 | |||
|- | |||
|ICTCybEnterprisesICT%SecPolicyDataLoss | |||
|Percent of enterprises which have an ICT security policy whose security policy addressed the risks of destruction or corruption of data due to an attack or by unexpected incident. | |||
|Percent of enterprises which have an ICT security policy whose security policy addressed the risks of destruction or corruption of data due to an attack or by unexpected incident. | |||
|5/6/2015 | |||
| | |||
|0 | |||
|- | |||
|ICTCybEnterprisesICT%SecPolicyOutThreat | |||
|Percent of enterprises which have an ICT security policy whose security policy addressed the risks of unavailability of ICT services due to an attack from outside (e.g. Denial of Service attack). | |||
|Percent of enterprises which have an ICT security policy whose security policy addressed the risks of unavailability of ICT services due to an attack from outside (e.g. Denial of Service attack). | |||
|5/6/2015 | |||
| | |||
|0 | |||
|- | |||
|ICTCybIndividual%FinLoss | |||
|The percentage of individuals that suffered a financial loss as a result of receiving fraudulent messages ('phishing') or getting redirected to fake websites asking for personal information ('pharming'). | |||
|he percentage of individuals that suffered a financial loss as a result of receiving fraudulent messages ('phishing') or getting redirected to fake websites asking for personal information ('pharming'). | |||
|5/5/2015 | |||
| | |||
|0 | |||
|- | |||
|ICTCybIndividual%FraudPay | |||
|The percentage of individuals that suffered a financial loss due to fraudulent payment (credit or debit) card use. | |||
|The percentage of individuals that suffered a financial loss due to fraudulent payment (credit or debit) card use. | |||
|5/5/2015 | |||
| | |||
|0 | |||
|- | |||
|ICTCybIndividual%PersonalInfoAbused | |||
|The percentage of individuals that suffered from an abuse of personal information sent on the Internet and/or other privacy violations (e.g. abuse of pictures, videos, personal data uploaded on community websites). | |||
|The percentage of individuals that suffered from an abuse of personal information sent on the Internet and/or other privacy violations (e.g. abuse of pictures, videos, personal data uploaded on community websites). | |||
|5/5/2015 | |||
| | |||
|0 | |||
|- | |||
|ICTCybIndividual%Spam | |||
|The percentage of individuals that received unsolicited emails ('Spam'). | |||
|The percentage of individuals that received unsolicited emails ('Spam'). | |||
|5/5/2015 | |||
| | |||
|0 | |||
|- | |||
|ICTCybIndividual%Virus | |||
|The percentage of individuals that caught a virus or other computer infection (e.g. worm or Trojan horse) resulting in loss of information or time. | |||
|The percentage of individuals that caught a virus or other computer infection (e.g. worm or Trojan horse) resulting in loss of information or time. | |||
|5/5/2015 | |||
| | |||
|0 | |||
|- | |||
|ICTCybIndividualIU%FinLoss | |||
|The percentage of individuals using the internet in the previous year that suffered a financial loss as a result of receiving fraudulent messages ('phishing') or getting redirected to fake websites asking for personal information ('pharming'). | |||
|The percentage of individuals using the internet in the previous year that suffered a financial loss as a result of receiving fraudulent messages ('phishing') or getting redirected to fake websites asking for personal information ('pharming'). | |||
|5/5/2015 | |||
| | |||
|0 | |||
|- | |||
|ICTCybIndividualIU%FraudPay | |||
|The percentage of individuals using the internet in the previous year that suffered a financial loss due to fraudulent payment (credit or debit) card use. | |||
|The percentage of individuals using the internet in the previous year that suffered a financial loss due to fraudulent payment (credit or debit) card use. | |||
|5/5/2015 | |||
| | |||
|0 | |||
|- | |||
|ICTCybIndividualIU%PersonalInfoAbused | |||
|The percentage of individuals using the internet in the previous year that suffered from an abuse of personal information sent on the Internet and/or other privacy violations (e.g. abuse of pictures, videos, personal data uploaded on community websites). | |||
|The percentage of individuals using the internet in the previous year that suffered from an abuse of personal information sent on the Internet and/or other privacy violations (e.g. abuse of pictures, videos, personal data uploaded on community websites). | |||
|5/5/2015 | |||
| | |||
|0 | |||
|- | |||
|ICTCybIndividualIU%Spam | |||
|The percentage of individuals that used the internet in the previous year that received unsolicited emails ('Spam'). | |||
|The percentage of individuals that used the internet in the previous year that received unsolicited emails ('Spam'). | |||
|5/5/2015 | |||
| | |||
|0 | |||
|- | |||
|ICTCybIndividualIU%Virus | |||
|The percentage of individuals that used the internet in the previous year that caught a virus or other computer infection (e.g. worm or Trojan horse) resulting in loss of information or time. | |||
|The percentage of individuals that used the internet in the previous year that caught a virus or other computer infection (e.g. worm or Trojan horse) resulting in loss of information or time. | |||
|5/5/2015 | |||
| | |||
|0 | |||
|- | |||
|ICTDSLFirmEStat | |||
|% of total firms using DSL Internet connection | |||
|% of total firms using DSL Internet Connection, without financial sector | |||
|2/14/2009 | |||
|% of total firms using DSL Internet Connection, without financial sector | |||
|0 | |||
|- | |||
|ICTDSLFirmIIACEStat | |||
|% of total firms with internet connections using DSL | |||
|% of total firms with internet connections using DSL, without financial sector | |||
|2/15/2009 | |||
|% of total firms with internet connections using DSL, without financial sector | |||
|0 | |||
|- | |||
|ICTDSLHouseholdEStat | |||
|% of total households using DSL internet connection | |||
|% of total households using DSL internet connection | |||
|2/15/2009 | |||
|% of total households using DSL internet connection | |||
|0 | |||
|- | |||
|ICTDSLHouseholdIIACEStat | |||
|% of total households with internet access using DSL | |||
|% of total households with internet access using DSL | |||
|2/15/2009 | |||
|% of total households with internet access using DSL | |||
|0 | |||
|- | |||
|ICTInternetAccessFirmcuseEStat | |||
|% of firms with internet access that use a computer | |||
|% of firms with internet access that use a computer | |||
|3/1/2009 | |||
|% of firms with internet access that use a computer | |||
|0 | |||
|- | |||
|ICTInternetAccessFirmEStat | |||
|% of total firms with internet access | |||
|% of total firms with internet access | |||
|3/1/2009 | |||
|% of total firms with internet access | |||
|0 | |||
|- | |||
|ICTInternetFirmEStat | |||
|% of total firms using other fixed connection | |||
|% of total firms using other fixed connection, e.g. cable UMTS, etc. | |||
|3/1/2009 | |||
|% of total firms using other fixed connection, e.g. cable UMTS, etc. | |||
|0 | |||
|- | |||
|ICTInternetFirmIIACEStat | |||
|% of firms with internet access using other fixed connection | |||
|% of firms with internet access using other fixed connection, e.g. cable UMTS, etc. | |||
|3/1/2009 | |||
|% of firms with internet access using other fixed connection, e.g. cable | |||
|0 | |||
|- | |||
|ICTInternetHouseholdEStat | |||
|% of households using other broadband connection | |||
|% of households using other broadband connection (e.g. cable UMTS, etc) | |||
|2/15/2009 | |||
|% of households using other broadband connection (e.g. cable UMTS, etc) | |||
|0 | |||
|- | |||
|ICTInternetHouseholdIIACEStat | |||
|% of households with internet access using other broadband connection | |||
|% of households with internet access using other broadband connection (e.g. cable UMTS, etc) | |||
|2/15/2009 | |||
|% of households with internet access using other broadband connection (e.g. cable UMTS, etc) | |||
|0 | |||
|- | |||
|ICTInternetUseHouseholdEStat | |||
|% of total households with internet access | |||
|% of total households with internet access | |||
|3/1/2009 | |||
|% of total firms with internet access | |||
|0 | |||
|} | |||
= Data Pulling Instructions = | |||
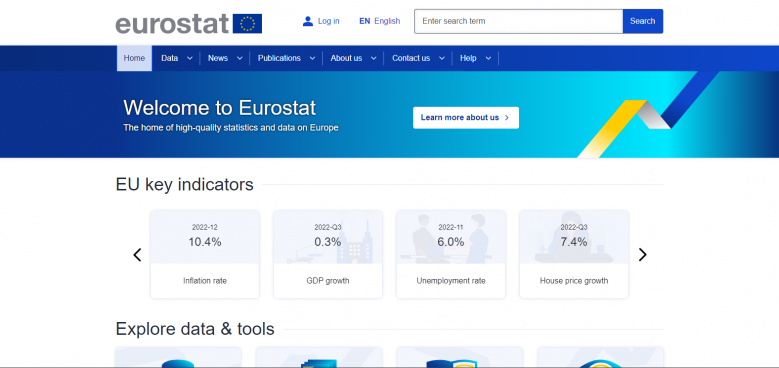
1. First, navigate to https://ec.europa.eu/eurostat/web/main/home. | 1. First, navigate to https://ec.europa.eu/eurostat/web/main/home. | ||
[[File:SOURCE IMG STEP 01.png|center|thumb|779x779px|Landing page for link above]] | [[File:SOURCE IMG STEP 01.png|center|thumb|779x779px|Landing page for link above]] | ||
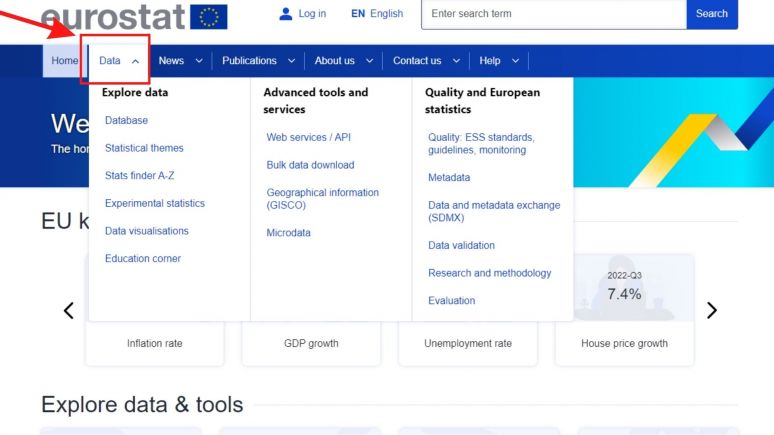
2. Hover over the "Data" tab with your cursor to expand the data tab options.[[File:Step2.jpg|center|thumb|774x774px]] | 2. Hover over the "Data" tab with your cursor to expand the data tab options.[[File:Step2.jpg|center|thumb|774x774px]] | ||
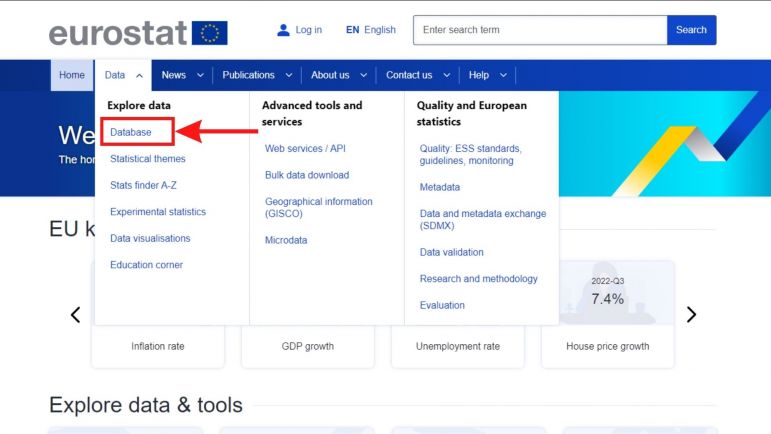
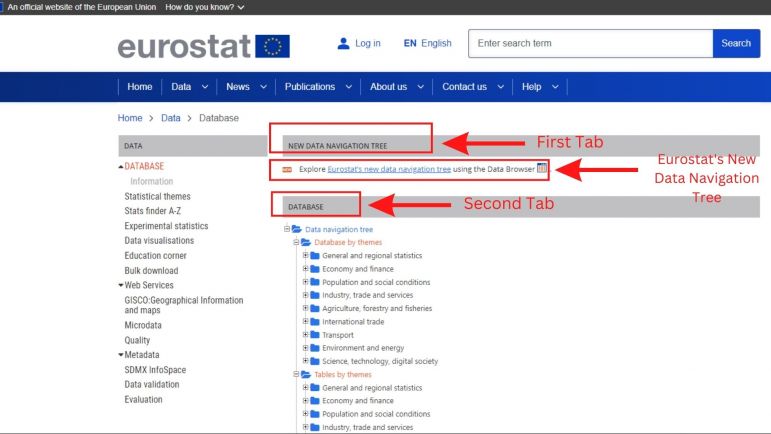
3. Under Data, click on the database tab which will take you to a new page.[[File:Step3.jpg|alt=Screenshot of database tab|center|thumb|771x771px|Screenshot of the database tab.]]4. In the database landing page, you will see two tabs. One called "NEW DATA NAVIGATION TREE" and another tab called "DATABASE" which contains different themes and topic for data series. The New Data Navigation Tree tool under the first tab is user friendly and allows you to easily find data series by general topics, so we will rely on it in this example. See screenshot below. | 3. Under Data, click on the database tab which will take you to a new page.[[File:Step3.jpg|alt=Screenshot of database tab|center|thumb|771x771px|Screenshot of the database tab.]]4. In the database landing page, you will see two tabs. One called "NEW DATA NAVIGATION TREE" and another tab called "DATABASE" which contains different themes and topic for data series. The New Data Navigation Tree tool under the first tab is user friendly and allows you to easily find data series by general topics, so we will rely on it in this example. See screenshot below. | ||
[[File:Step 4 .jpg|center|thumb|771x771px|Screenshot of first and second tab and Eurostat's New Navigation Tree tool.]] | [[File:Step 4 .jpg|center|thumb|771x771px|Screenshot of first and second tab and Eurostat's New Navigation Tree tool.]] | ||
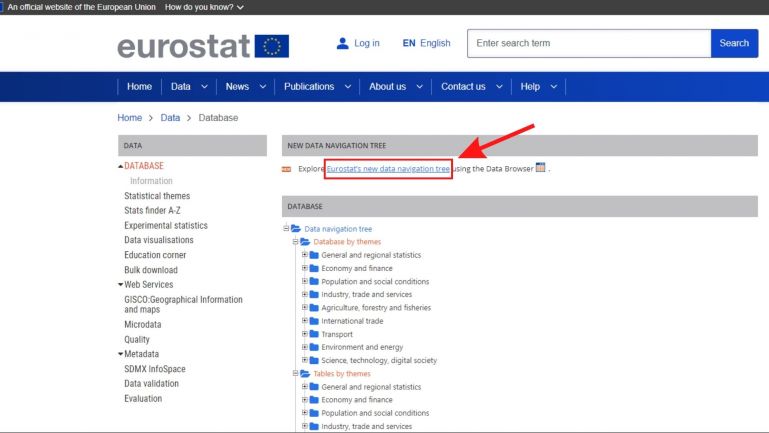
5. Click on Eurostat's new data navigation tree hyperlink. | |||
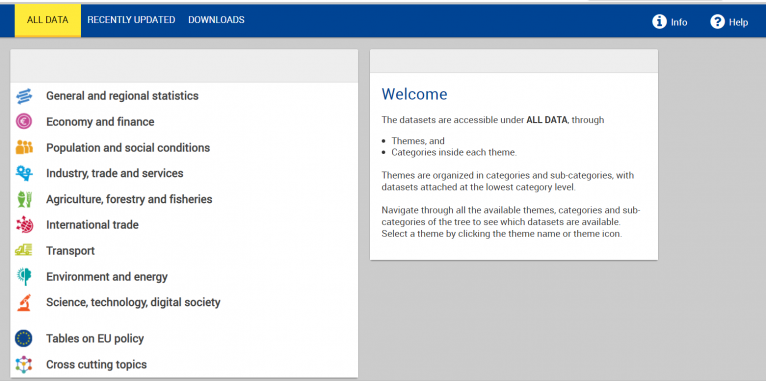
[[File:Step5.jpg|center|thumb|769x769px|Screenshot of Eurostat's new data navigation tree hyperlink.]] | 5. Click on Eurostat's new data navigation tree hyperlink. [[File:Step5.jpg|center|thumb|769x769px|Screenshot of Eurostat's new data navigation tree hyperlink.]]6. Once you are on the new data navigation tree page, you may choose the category your series is in.[[File:SOURCE IMG STEP 05.png|center|thumb|766x766px|Category selection]] | ||
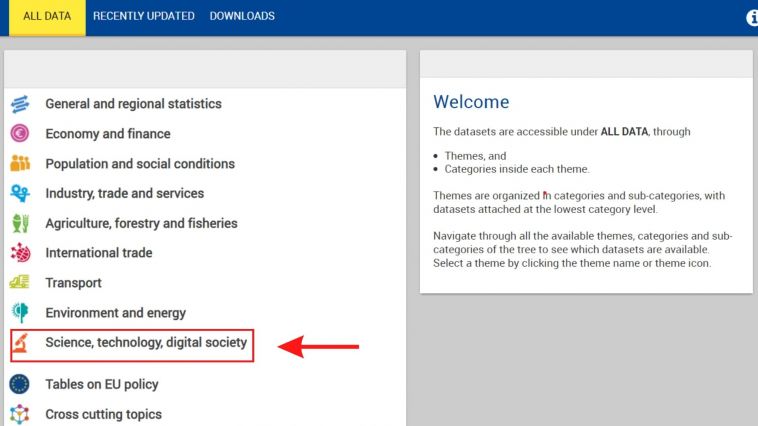
[[File: | == VARIABLE EXAMPLE: SeriesICTBroadbandHouseholdEStat == | ||
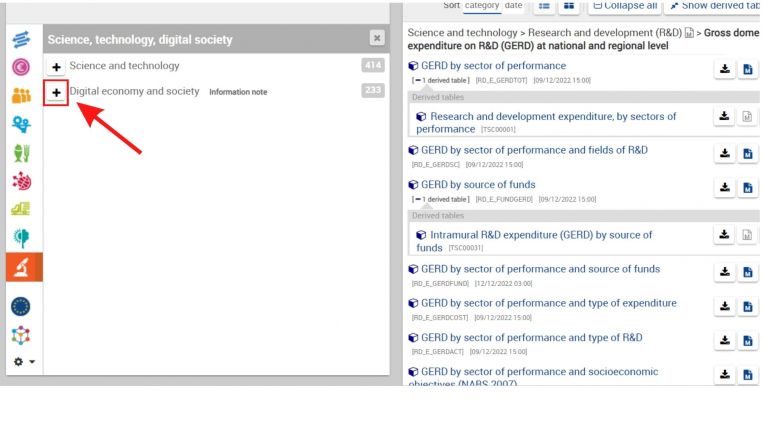
[[File: | 7. Once on the new landing page, you may choose any of the topics to find your data series. In this example, we will click on the "Science, technology, digital society" tab to find the variable SeriesICTBroadbandHouseholdEStat.[[File:SOURCE IMG STEP 07.jpg|center|thumb|758x758px|Category selection]]8. After clicking on "Science, technology, and digital society", we will expand the "Digital economy and society" tab by clicking on the + symbol on the left.[[File:SOURCE IMG STEP 08.jpg|center|thumb|763x763px|Click + symbol]] | ||
[[File: | |||
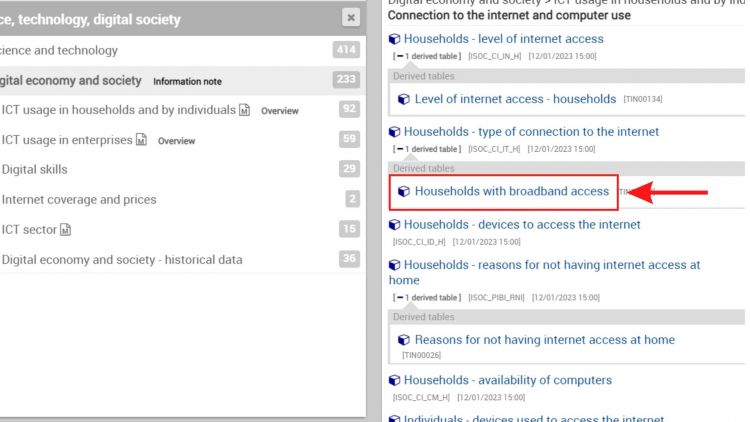
9. After expanding the tab, series will populate on the right-hand side of the screen. Find your series and click on the hyperlink to view the data.[[File:SOURCE IMG STEP 09.jpg|center|thumb|750x750px|Click on hyperlink for series]] | |||
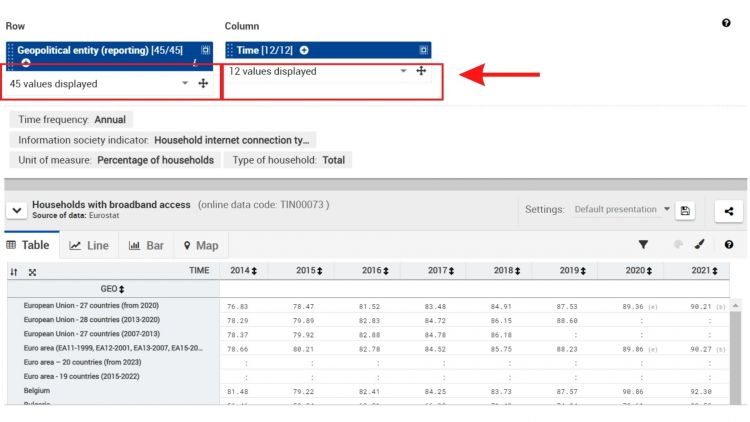
10. After clicking on "Households with broadband access", you will be able to see the data series and may manipulate the country and years selection by clicking on the drop down menu for each.[[File:SOURCE IMG STEP 10.jpg|center|thumb|750x750px|Change year/country selection]] | |||
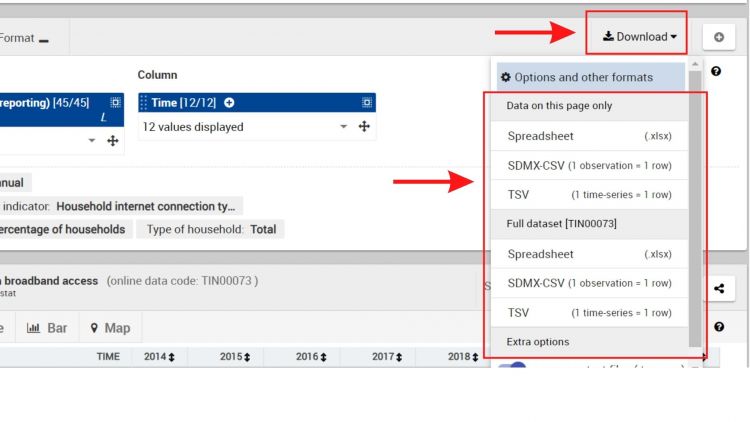
11. To download the desired selection, click on download and select the desired file type (e.g., csv).[[File:SOURCE IMG STEP 11.jpg|center|thumb|750x750px|Format and download]] | |||
= Data Notes = | |||
Latest revision as of 15:20, 11 July 2025
Summary
Eurostat is a Directorate-General of the European Commission which is the statistical office of the European Union (EU). Eurostat collects and publishes aggregate data on various variables in EU countries. Users can rely on the Eurostat database to find a number of data series and variables such as: SeriesICTCybEnterprises%ISDNConnection, SeriesICTCybEnterprises%MobileBroadbandConnection, SeriesICTCybEnterprises%SecFacOffStorage, and SeriesICTCybEnterprisesC%SecPolicyDataLoss.
Tables In IFs
| Variables | Definition | Source Ext Def | LastIFsUpdate | Name In Source | UsedInPreprocessor |
|---|---|---|---|---|---|
| PovRateNPLBothSexesEuroStat | At risk of poverty rate (cut-off point: 60% of median equivalised income after social transfers), all ages, both sexes, from EuroStat | 7/5/2021 | Income and living conditions indicator: At risk of poverty rate | 0 | |
| PovRateNPLFemaleEuroStat | At risk of poverty rate (cut-off point: 60% of median equivalised income after social transfers), all ages, female, from EuroStat | 7/5/2021 | Income and living conditions indicator: At risk of poverty rate | 0 | |
| PovRateNPLMaleEuroStat | At risk of poverty rate (cut-off point: 60% of median equivalised income after social transfers), all ages, male, from EuroStat | 7/5/2021 | Income and living conditions indicator: At risk of poverty rate | 0 | |
| ICTVA%GDP | ICT value added as % of GDP | OECD Key ICT Indicators, 10b. R&D expenditure in selected ICT industries, 2005contact Geomina, Geomina.TURLEA@ec.europa.eu and Jonathan Moyer | 9/14/2010 | 0 | |
| R&Dbus%GDP | R&D, business expenditure as a % of GDP | contact Geomina, Geomina.TURLEA@ec.europa.eu and Jonathan Moyer | 9/14/2010 | 0 | |
| R&DICTBus%GDP | R&D in ICT, business expenditure, as a percentage of GDP | contact Geomina, Geomina.TURLEA@ec.europa.eu and Jonathan Moyer | 9/14/2010 | 0 | |
| R&DICTBus%ICTVA | R&D in ICT, business expenditure, as a % of ICT value added | contact Geomina, Geomina.TURLEA@ec.europa.eu and Jonathan Moyer | 9/14/2010 | 0 | |
| R&DICTBus%Total | R&D in ICT, business expenditure, as a % of total business expenditure on R & D | contact Geomina, Geomina.TURLEA@ec.europa.eu and Jonathan Moyer | 9/14/2010 | 0 | |
| R&DICTGovt%GDP | R&D in ICT, public expenditure, as a % of GDP | OECD Key ICT Indicators, 10b. R&D expenditure in selected ICT industries, 2005contact Geomina, Geomina.TURLEA@ec.europa.eu and Jonathan Moyer | 9/14/2010 | 0 | |
| ICTBroadbandHouseholdEStat | % of households using a broadband connection | % of hhs using a broadband connection | 2/15/2009 | % of hhs using a broadband connection | 0 |
| ICTBroadbandHouseholdIIACEStat | % of households with internet access using a broadband connection | % of households with internet access using a broadband connection | 2/15/2009 | % of households with internet access using a broadband connection | 0 |
| ICTBuyOnlineIndividual | % of individuals with internet access that have ordered via internet over last calendar year | % of individuals with internet access that have ordered via internet over last calendar year | 3/1/2009 | % of firms with internet access that have ordered via internet over last calendar year | 0 |
| ICTCybEnterprises%ISDNConnection | The percentage of enterprises connecting to the Internet via ISDN | The percentage of enterprises connecting to the Internet via ISDN. | 5/5/2015 | 0 | |
| ICTCybEnterprises%MobileBroadbandConnection | The percentage of enterprises connecting to the Internet via a mobile broadband connection (3G modem or 3G handset). | The percentage of enterprises connecting to the Internet via a mobile broadband connection (3G modem or 3G handset). | 5/5/2015 | 0 | |
| ICTCybEnterprises%MobileConnection | The percentage of enterprises connecting to the Internet via a mobile connection (e.g. mobile phone, GPRS, UMTS, etc.). | The percentage of enterprises connecting to the Internet via a mobile connection (e.g. mobile phone, GPRS, UMTS, etc.). | 5/5/2015 | 0 | |
| ICTCybEnterprises%MobileConnection2014 | The percentage of enterprises connecting to the Internet via mobile connection (broadband or other mobile connection) | The percentage of enterprises connecting to the Internet via mobile connection (broadband or other mobile connection) | 5/5/2015 | 0 | |
| ICTCybEnterprises%ModemConnection | The percentage of enterprises connecting to the Internet via modem (dial-up access over normal telephone line). | The percentage of enterprises connecting to the Internet via modem (dial-up access over normal telephone line). | 5/5/2015 | 0 | |
| ICTCybEnterprises%SecFacID | Percent of enterprises using strong password authentication (min 8 characters, max 6 months, encrypted transmission and storage) and user identification and authentication via hardware tokens, e.g. smart cards | Percent of enterprises using strong password authentication (min 8 characters, max 6 months, encrypted transmission and storage) and user identification and authentication via hardware tokens, e.g. smart cards | 5/6/2015 | 0 | |
| ICTCybEnterprises%SecFacIDHW | Percent of enterprises using user identification and authentication via hardware tokens, e.g. smart cards | Percent of enterprises using user identification and authentication via hardware tokens, e.g. smart cards | 5/6/2015 | 0 | |
| ICTCybEnterprises%SecFacLog | Percent of enterprises logging activities for analyses of security incidents | Percent of enterprises logging activities for analyses of security incidents | 5/6/2015 | 0 | |
| ICTCybEnterprises%SecFacOffStorage | Percent of enterprises storing data backups offsite | Percent of enterprises storing data backups offsite | 5/6/2015 | 0 | |
| ICTCybEnterprises%SecFacPW | Percent of enterprises using strong password authentication (min 8 characters, max 6 months, encrypted transmission and storage) | Percent of enterprises using strong password authentication (min 8 characters, max 6 months, encrypted transmission and storage) | 5/6/2015 | 0 | |
| ICTCybEnterprises%SecIncidentAllEx | Percent of enterprises that exxperienced any ICT related security incidents excluding disclosure of confidential data in electronic form by employees. | Percent of enterprises that exxperienced any ICT related security incidents excluding disclosure of confidential data in electronic form by employees. | 5/6/2015 | 0 | |
| ICTCybEnterprises%SecIncidentConfData | Percent of enterprises that experienced ICT related security incidents that resulted in disclosure of confidential data due to intrusion, pharming, phishing attacks. | Percent of enterprises that experienced ICT related security incidents that resulted in disclosure of confidential data due to intrusion, pharming, phishing attacks. | 5/6/2015 | 0 | |
| ICTCybEnterprises%SecIncidentDataLoss | Percent of enterprises that experienced ICT related security incidents that resulted in destruction or corruption of data due to infection or malicious software or unauthorised access. | Percent of enterprises that experienced ICT related security incidents that resulted in destruction or corruption of data due to infection or malicious software or unauthorised access. | 5/6/2015 | 0 | |
| ICTCybEnterprises%SecIncidentEmploy | Percent of enterprises that experienced ICT related security incidents resulting in disclosure of confidential data in electronic form by employees whether on intention or unintentionally. | Percent of enterprises that experienced ICT related security incidents resulting in disclosure of confidential data in electronic form by employees whether on intention or unintentionally. | 5/6/2015 | 0 | |
| ICTCybEnterprises%SecIncidentNone | Percent of enterprises that did not experience any ICT related security incidents excluding disclosure of confidential data in electronic form by employees. | Percent of enterprises that did not experience any ICT related security incidents excluding disclosure of confidential data in electronic form by employees. | 5/6/2015 | 0 | |
| ICTCybEnterprises%SecIncidentOutThreat | Percent of enterprises that experienced ICT related security incidents that resulted in unavailability of ICT services due to attacks from outside, e.g. Denial of Service attack. | Percent of enterprises that experienced ICT related security incidents that resulted in unavailability of ICT services due to attacks from outside, e.g. Denial of Service attack. | 5/6/2015 | 0 | |
| ICTCybEnterprises%SecIncidentSystemFailure | Percent of enterprises that experienced ICT related security incidents that resulted in unavailability of ICT services, destruction or corruption of data due to hardware or software failures. | Percent of enterprises that experienced ICT related security incidents that resulted in unavailability of ICT services, destruction or corruption of data due to hardware or software failures. | 5/6/2015 | 0 | |
| ICTCybEnterprises%SecPolicy | Percent of enterprises that have a formally defined ICT security policy with a plan of regular review. | Percent of enterprises that have a formally defined ICT security policy with a plan of regular review. | 5/6/2015 | 0 | |
| ICTCybEnterprises%SecPolicyAll | Percent of enterprises whose ICT security policy addressed the risks of destruction or corruption of data, disclosure of confidential data and unavailability of ICT services due to an attack or an accident. | Percent of enterprises whose ICT security policy addressed the risks of destruction or corruption of data, disclosure of confidential data and unavailability of ICT services due to an attack or an accident. | 5/6/2015 | 0 | |
| ICTCybEnterprises%SecPolicyConfData | Percent of enterprises whose ICT security policy addressed the risks of disclosure of confidential data due to intrusion, pharming, phishing attacks or by accident. | Percent of enterprises whose ICT security policy addressed the risks of disclosure of confidential data due to intrusion, pharming, phishing attacks or by accident. | 5/6/2015 | 0 | |
| ICTCybEnterprises%SecPolicyDataLoss | Percent of enterprises whose ICT security policy addressed the risks of destruction or corruption of data due to an attack or by unexpected incident. | Percent of enterprises whose ICT security policy addressed the risks of destruction or corruption of data due to an attack or by unexpected incident. | 5/6/2015 | 0 | |
| ICTCybEnterprises%SecPolicyOutThreat | Percent of enterprises whose ICT security policy addressed the risks of unavailability of ICT services due to an attack from outside (e.g. Denial of Service attack). | Percent of enterprises whose ICT security policy addressed the risks of unavailability of ICT services due to an attack from outside (e.g. Denial of Service attack). | 5/6/2015 | 0 | |
| ICTCybEnterprises%Website | The percentage of enterprises that have a website or homepage. | The percentage of enterprises that have a website or homepage. | 5/5/2015 | 0 | |
| ICTCybEnterprises%WirelessConnection | The percentage of all enterprises connecting to the Internet via wireless connection (satellite, mobile phone). | The percentage of all enterprises connecting to the Internet via wireless connection (satellite, mobile phone). | 5/5/2015 | 0 | |
| ICTCybEnterprisesC%SecFacID | Percent of enterprises with computers using strong password authentication (min 8 characters, max 6 months, encrypted transmission and storage) and user identification and authentication via hardware tokens, e.g. smart cards | Percent of enterprises using strong password authentication (min 8 characters, max 6 months, encrypted transmission and storage) and user identification and authentication via hardware tokens, e.g. smart cards | 5/6/2015 | 0 | |
| ICTCybEnterprisesC%SecFacIDHW | Percent of enterprises with computers using user identification and authentication via hardware tokens, e.g. smart cards | Percent of enterprises using user identification and authentication via hardware tokens, e.g. smart cards | 5/6/2015 | 0 | |
| ICTCybEnterprisesC%SecFacLog | Percent of enterprises with computers logging activities for analyses of security incidents | Percent of enterprises logging activities for analyses of security incidents | 5/6/2015 | 0 | |
| ICTCybEnterprisesC%SecFacOffStorage | Percent of enterprises with computers storing data backups offsite | Percent of enterprises storing data backups offsite | 5/6/2015 | 0 | |
| ICTCybEnterprisesC%SecFacPW | Percent of enterprises with computers using strong password authentication (min 8 characters, max 6 months, encrypted transmission and storage) | Percent of enterprises using strong password authentication (min 8 characters, max 6 months, encrypted transmission and storage) | 5/6/2015 | 0 | |
| ICTCybEnterprisesC%SecIncidentAllEx | Percent of enterprises with computers that experienced any ICT related security incidents excluding disclosure of confidential data in electronic form by employees. | Percent of enterprises with computers that experienced any ICT related security incidents excluding disclosure of confidential data in electronic form by employees. | 5/6/2015 | 0 | |
| ICTCybEnterprisesC%SecIncidentConfData | Percent of enterprises with computers that experienced ICT related security incidents that resulted in disclosure of confidential data due to intrusion, pharming, phishing attacks. | Percent of enterprises with computers that experienced ICT related security incidents that resulted in disclosure of confidential data due to intrusion, pharming, phishing attacks. | 5/6/2015 | 0 | |
| ICTCybEnterprisesC%SecIncidentDataLoss | Percent of enterprises with computers that experienced ICT related security incidents that resulted in destruction or corruption of data due to infection or malicious software or unauthorised access. | Percent of enterprises with computers that experienced ICT related security incidents that resulted in destruction or corruption of data due to infection or malicious software or unauthorised access. | 5/6/2015 | 0 | |
| ICTCybEnterprisesC%SecIncidentEmploy | Percent of enterprises with computers that experienced ICT related security incidents resulting in disclosure of confidential data in electronic form by employees whether on intention or unintentionally. | Percent of enterprises with computers that experienced ICT related security incidents resulting in disclosure of confidential data in electronic form by employees whether on intention or unintentionally. | 5/6/2015 | 0 | |
| ICTCybEnterprisesC%SecIncidentNone | Percent of enterprises with computers that did not experienced any ICT related security incidents excluding disclosure of confidential data in electronic form by employees. | Percent of enterprises with computers that did not experienced any ICT related security incidents excluding disclosure of confidential data in electronic form by employees. | 5/6/2015 | 0 | |
| ICTCybEnterprisesC%SecIncidentOutThreat | Percent of enterprises with computers that experienced ICT related security incidents that resulted in unavailability of ICT services due to attacks from outside, e.g. Denial of Service attack. | Percent of enterprises with computers that experienced ICT related security incidents that resulted in unavailability of ICT services due to attacks from outside, e.g. Denial of Service attack. | 5/6/2015 | 0 | |
| ICTCybEnterprisesC%SecIncidentSystemFailure | Percent of enterprises with computers that experienced ICT related security incidents that resulted in unavailability of ICT services, destruction or corruption of data due to hardware or software failures. | Percent of enterprises with computers that experienced ICT related security incidents that resulted in unavailability of ICT services, destruction or corruption of data due to hardware or software failures. | 5/6/2015 | 0 | |
| ICTCybEnterprisesC%SecPolicy | Percent of enterprises which use computers that have a formally defined ICT security policy with a plan of regular review. | Percent of enterprises that have a formally defined ICT security policy with a plan of regular review. | 5/6/2015 | 0 | |
| ICTCybEnterprisesC%SecPolicyAll | Percent of enterprises which use computers whose ICT security policy addressed the risks of destruction or corruption of data, disclosure of confidential data and unavailability of ICT services due to an attack or an accident. | Percent of enterprises which use computers whose ICT security policy addressed the risks of destruction or corruption of data, disclosure of confidential data and unavailability of ICT services due to an attack or an accident. | 5/6/2015 | 0 | |
| ICTCybEnterprisesC%SecPolicyConfData | Percent of enterprises which use computers whose ICT security policy addressed the risks of disclosure of confidential data due to intrusion, pharming, phishing attacks or by accident. | Percent of enterprises which use computers whose ICT security policy addressed the risks of disclosure of confidential data due to intrusion, pharming, phishing attacks or by accident. | 5/6/2015 | 0 | |
| ICTCybEnterprisesC%SecPolicyDataLoss | Percent of enterprises which use computers whose ICT security policy addressed the risks of destruction or corruption of data due to an attack or by unexpected incident. | Percent of enterprises which use computers whose ICT security policy addressed the risks of destruction or corruption of data due to an attack or by unexpected incident. | 5/6/2015 | 0 | |
| ICTCybEnterprisesC%SecPolicyOutThreat | Percent of enterprises which use computers whose ICT security policy addressed the risks of unavailability of ICT services due to an attack from outside (e.g. Denial of Service attack). | Percent of enterprises which use computers whose ICT security policy addressed the risks of unavailability of ICT services due to an attack from outside (e.g. Denial of Service attack). | 5/6/2015 | 0 | |
| ICTCybEnterprisesIA%ISDNConnection | The percentage of enterprises with internet access connecting to the Internet via ISDN | The percentage of enterprises with internet access connecting to the Internet via ISDN | 5/5/2015 | 0 | |
| ICTCybEnterprisesIA%MobileBroadbandConnection | The percentage of enterprises with internet access connecting to the Internet via a mobile broadband connection (3G modem or 3G handset). | The percentage of enterprises with internet access connecting to the Internet via a mobile broadband connection (3G modem or 3G handset). | 5/5/2015 | 0 | |
| ICTCybEnterprisesIA%MobileConnection | The percentage of enterprises with internet access connecting to the Internet via a mobile connection (e.g. mobile phone, GPRS, UMTS, etc.). | The percentage of enterprises with internet access connecting to the Internet via a mobile connection (e.g. mobile phone, GPRS, UMTS, etc.). | 5/5/2015 | 0 | |
| ICTCybEnterprisesIA%MobileConnection2014 | The percentage of enterprises with internet access connecting to the Internet via mobile connection (broadband or other mobile connection) | The percentage of enterprises with internet access connecting to the Internet via mobile connection (broadband or other mobile connection) | 5/5/2015 | 0 | |
| ICTCybEnterprisesIA%ModemConnection | The percentage of enterprises with internet access connecting to the Internet via modem (dial-up access over normal telephone line). | The percentage of enterprises with internet access connecting to the Internet via modem (dial-up access over normal telephone line). | 5/5/2015 | 0 | |
| ICTCybEnterprisesIA%WirelessConnection | The percentage of enterprises with internet access connecting to the Internet via wireless connection (satellite, mobile phone). | The percentage of enterprises with internet access connecting to the Internet via wireless connection (satellite, mobile phone). | 5/5/2015 | 0 | |
| ICTCybEnterprisesICT%SecPolicyAll | Percent of enterprises which have an ICT security policy whose security policy addressed the risks of destruction or corruption of data, disclosure of confidential data and unavailability of ICT services due to an attack or an accident. | Percent of enterprises which have an ICT security policy whose security policy addressed the risks of destruction or corruption of data, disclosure of confidential data and unavailability of ICT services due to an attack or an accident. | 5/6/2015 | 0 | |
| ICTCybEnterprisesICT%SecPolicyConfData | Percent of enterprises which have an ICT security policy whose security policy addressed the risks of disclosure of confidential data due to intrusion, pharming, phishing attacks or by accident. | Percent of enterprises which have an ICT security policy whose security policy addressed the risks of disclosure of confidential data due to intrusion, pharming, phishing attacks or by accident. | 5/6/2015 | 0 | |
| ICTCybEnterprisesICT%SecPolicyDataLoss | Percent of enterprises which have an ICT security policy whose security policy addressed the risks of destruction or corruption of data due to an attack or by unexpected incident. | Percent of enterprises which have an ICT security policy whose security policy addressed the risks of destruction or corruption of data due to an attack or by unexpected incident. | 5/6/2015 | 0 | |
| ICTCybEnterprisesICT%SecPolicyOutThreat | Percent of enterprises which have an ICT security policy whose security policy addressed the risks of unavailability of ICT services due to an attack from outside (e.g. Denial of Service attack). | Percent of enterprises which have an ICT security policy whose security policy addressed the risks of unavailability of ICT services due to an attack from outside (e.g. Denial of Service attack). | 5/6/2015 | 0 | |
| ICTCybIndividual%FinLoss | The percentage of individuals that suffered a financial loss as a result of receiving fraudulent messages ('phishing') or getting redirected to fake websites asking for personal information ('pharming'). | he percentage of individuals that suffered a financial loss as a result of receiving fraudulent messages ('phishing') or getting redirected to fake websites asking for personal information ('pharming'). | 5/5/2015 | 0 | |
| ICTCybIndividual%FraudPay | The percentage of individuals that suffered a financial loss due to fraudulent payment (credit or debit) card use. | The percentage of individuals that suffered a financial loss due to fraudulent payment (credit or debit) card use. | 5/5/2015 | 0 | |
| ICTCybIndividual%PersonalInfoAbused | The percentage of individuals that suffered from an abuse of personal information sent on the Internet and/or other privacy violations (e.g. abuse of pictures, videos, personal data uploaded on community websites). | The percentage of individuals that suffered from an abuse of personal information sent on the Internet and/or other privacy violations (e.g. abuse of pictures, videos, personal data uploaded on community websites). | 5/5/2015 | 0 | |
| ICTCybIndividual%Spam | The percentage of individuals that received unsolicited emails ('Spam'). | The percentage of individuals that received unsolicited emails ('Spam'). | 5/5/2015 | 0 | |
| ICTCybIndividual%Virus | The percentage of individuals that caught a virus or other computer infection (e.g. worm or Trojan horse) resulting in loss of information or time. | The percentage of individuals that caught a virus or other computer infection (e.g. worm or Trojan horse) resulting in loss of information or time. | 5/5/2015 | 0 | |
| ICTCybIndividualIU%FinLoss | The percentage of individuals using the internet in the previous year that suffered a financial loss as a result of receiving fraudulent messages ('phishing') or getting redirected to fake websites asking for personal information ('pharming'). | The percentage of individuals using the internet in the previous year that suffered a financial loss as a result of receiving fraudulent messages ('phishing') or getting redirected to fake websites asking for personal information ('pharming'). | 5/5/2015 | 0 | |
| ICTCybIndividualIU%FraudPay | The percentage of individuals using the internet in the previous year that suffered a financial loss due to fraudulent payment (credit or debit) card use. | The percentage of individuals using the internet in the previous year that suffered a financial loss due to fraudulent payment (credit or debit) card use. | 5/5/2015 | 0 | |
| ICTCybIndividualIU%PersonalInfoAbused | The percentage of individuals using the internet in the previous year that suffered from an abuse of personal information sent on the Internet and/or other privacy violations (e.g. abuse of pictures, videos, personal data uploaded on community websites). | The percentage of individuals using the internet in the previous year that suffered from an abuse of personal information sent on the Internet and/or other privacy violations (e.g. abuse of pictures, videos, personal data uploaded on community websites). | 5/5/2015 | 0 | |
| ICTCybIndividualIU%Spam | The percentage of individuals that used the internet in the previous year that received unsolicited emails ('Spam'). | The percentage of individuals that used the internet in the previous year that received unsolicited emails ('Spam'). | 5/5/2015 | 0 | |
| ICTCybIndividualIU%Virus | The percentage of individuals that used the internet in the previous year that caught a virus or other computer infection (e.g. worm or Trojan horse) resulting in loss of information or time. | The percentage of individuals that used the internet in the previous year that caught a virus or other computer infection (e.g. worm or Trojan horse) resulting in loss of information or time. | 5/5/2015 | 0 | |
| ICTDSLFirmEStat | % of total firms using DSL Internet connection | % of total firms using DSL Internet Connection, without financial sector | 2/14/2009 | % of total firms using DSL Internet Connection, without financial sector | 0 |
| ICTDSLFirmIIACEStat | % of total firms with internet connections using DSL | % of total firms with internet connections using DSL, without financial sector | 2/15/2009 | % of total firms with internet connections using DSL, without financial sector | 0 |
| ICTDSLHouseholdEStat | % of total households using DSL internet connection | % of total households using DSL internet connection | 2/15/2009 | % of total households using DSL internet connection | 0 |
| ICTDSLHouseholdIIACEStat | % of total households with internet access using DSL | % of total households with internet access using DSL | 2/15/2009 | % of total households with internet access using DSL | 0 |
| ICTInternetAccessFirmcuseEStat | % of firms with internet access that use a computer | % of firms with internet access that use a computer | 3/1/2009 | % of firms with internet access that use a computer | 0 |
| ICTInternetAccessFirmEStat | % of total firms with internet access | % of total firms with internet access | 3/1/2009 | % of total firms with internet access | 0 |
| ICTInternetFirmEStat | % of total firms using other fixed connection | % of total firms using other fixed connection, e.g. cable UMTS, etc. | 3/1/2009 | % of total firms using other fixed connection, e.g. cable UMTS, etc. | 0 |
| ICTInternetFirmIIACEStat | % of firms with internet access using other fixed connection | % of firms with internet access using other fixed connection, e.g. cable UMTS, etc. | 3/1/2009 | % of firms with internet access using other fixed connection, e.g. cable | 0 |
| ICTInternetHouseholdEStat | % of households using other broadband connection | % of households using other broadband connection (e.g. cable UMTS, etc) | 2/15/2009 | % of households using other broadband connection (e.g. cable UMTS, etc) | 0 |
| ICTInternetHouseholdIIACEStat | % of households with internet access using other broadband connection | % of households with internet access using other broadband connection (e.g. cable UMTS, etc) | 2/15/2009 | % of households with internet access using other broadband connection (e.g. cable UMTS, etc) | 0 |
| ICTInternetUseHouseholdEStat | % of total households with internet access | % of total households with internet access | 3/1/2009 | % of total firms with internet access | 0 |
Data Pulling Instructions
1. First, navigate to https://ec.europa.eu/eurostat/web/main/home.
VARIABLE EXAMPLE: SeriesICTBroadbandHouseholdEStat
7. Once on the new landing page, you may choose any of the topics to find your data series. In this example, we will click on the "Science, technology, digital society" tab to find the variable SeriesICTBroadbandHouseholdEStat.